




Eric DeGrass
July 17th, 2024
In risk management, understanding the concept of residual risk is crucial for organizations striving toward operational excellence. To grasp this better, we can first draw an analogy to a familiar concept: the Circle of Knowledge where not knowing what you don’t know lays in wait to bring us down.
Imagine a circle representing your total knowledge. This circle can be divided into two segments: Things You Know and the Things You Don't Know
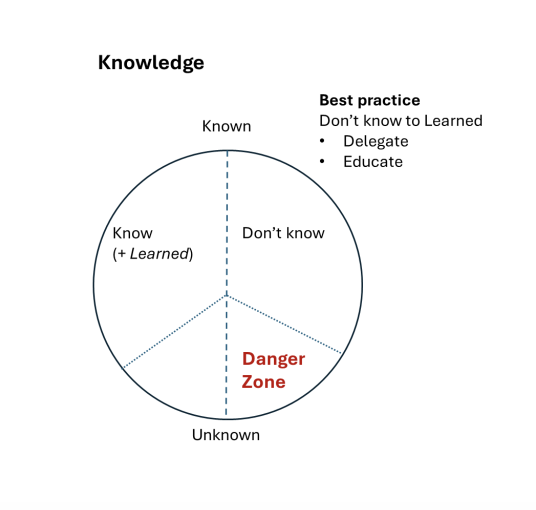
However, we need to delve deeper. We need to subdivide these segments again into:
Things You Know You Know
Things You Know You Don't Know
Things You Don't Know You Know
Things You Don't Know You Don't Know
The biggest threat lies in the "Things You Don't Know You Don't Know" sector. These unknown unknowns are perilous because they evade our awareness and preparedness. When we know what we don’t know, we can take steps to educate ourselves or delegate tasks to those with the necessary knowledge. The goal is to transform the unknowns into knowns.
Now let's consider a Circle of Risk. This circle can be divided into two broad categories: Acceptable Risk and Unacceptable Risk
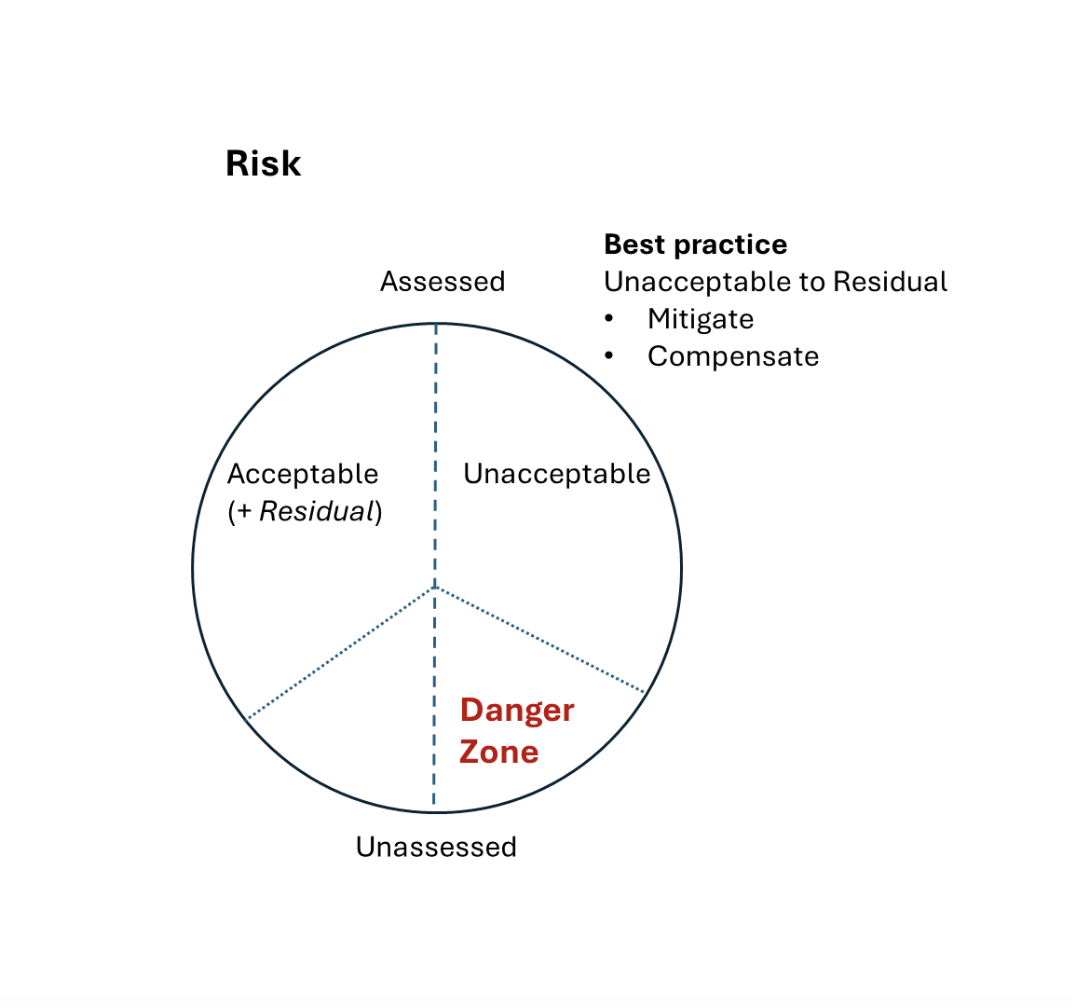
Similarly, these categories need to be further segmented into:
Assessed Acceptable Risk
Assessed Unacceptable Risk
Unassessed Acceptable Risk
Unassessed Unacceptable Risk
Just as with the Circle of Knowledge example, the danger zone in the Circle of Risk is the "Unassessed Unacceptable Risk." These are risks that have not been adequately evaluated.
Unlike knowledge, risk assessment is not a single step. Immaterial (or acceptable) risk must be validated and reassessed on an ongoing basis. In other words, there are two sources of unassessed risk:
Risks that have never been adequately assessed and (additionally),
Risks whose earlier assessments need to be validated or recalibrated.
The latter scenario is essential to capture changes in potential incident damage, likelihood of incident occurrence, and the cost and complexity of mitigating that risk. For example, the likelihood of phishing has increased with deep fakes, the damage from a systems outage has likely increased with increased dependence on shared cloud services, and the complexity and expense of mitigating these vulnerabilities may increase or decrease over time. Once a risk is properly assessed, it can be mitigated or compensated, transforming an unacceptable risk into an acceptable risk, or as it is commonly referred to, residual risk.
In recent years, regulatory bodies have placed a strong emphasis on the identification, documentation, and reassessment of residual risk. For instance, the Digital Operational Resilience Act (DORA) in the European Union requires financial institutions to manage and mitigate IT risks comprehensively. DORA mandates:
Clear Identification of Risks: Organizations must catalog all potential risks to their digital operations.
Documentation: Detailed documentation of identified risks and the measures taken to mitigate them.
Regular Reassessment: Continuous evaluation to ensure that residual risks have not evolved into unacceptable risks (Preamble 1-8)
Other operational resilience regulations, such as the UK's Operational Resilience Framework and the US Federal Reserve’s guidelines, also stress the importance of a proactive and ongoing approach to risk management. These regulations require organizations to:
Establish a Robust Risk Management Framework: Implement processes that identify, assess, and manage risks effectively.
Engage in Continuous Improvement: Regularly update risk assessments and mitigation strategies to adapt to changing environments and emerging threats.
System integrity and operational resilience can be threatened by malicious exploits and through non-security related system and platform bugs. Assessing the materiality (likelihood, damage, and cost of mitigation) is required for both categories – and their relative risk must be documented and re–established on an ongoing basis. This includes:
Regular Reassessment and Documentation: Potential risks must be reassessed and documented regularly.
Contextual Decision-Making: Risks that become unacceptable over time must be mitigated or compensated for based on a reasonable assessment.
Comprehensive Evaluation: This assessment should include:
The potential damage of an outage.
The likelihood of such an outage being triggered by a non-security related bug.
The effort and cost required to mitigate or compensate for that risk (Articles 10, 11, 25, 30, 33)
The analogy of the Circle of Knowledge and the Circle of Risk underscores the critical importance of awareness and assessment in risk management. Unassessed unacceptable risks are akin to unknown unknowns—they are the unseen dangers that can undermine an organization. By committing to identifying and evaluating all potential risks, organizations can transform unacceptable risks into manageable residual risks, ensuring a safer and more resilient operational environment.
Regulatory bodies across the globe recognize the criticality of continuously monitoring residual risk and have included best practices in their requirements and guidelines.


Eric DeGrass
October 21st, 2025


Eric DeGrass
September 24th, 2025
Sign up to receive a monthly email with stories and guidance on getting proactive with vendor risk
BugZero requires your corporate email address to provide you with updates and insights about the BugZero solution, Operational Defect Database (ODD), and other IT Operational Resilience matters. As fellow IT people, we hate spam too. We prioritize the security of your personal information and will only reach out only once a month with pertinent and valuable content.
You may unsubscribe from these communications at anytime. For information on how to unsubscribe, as well as our privacy practices and commitment to protecting your privacy, check out our Privacy Policy.


Eric DeGrass
October 16th, 2025